'via Blog this'
Tech News
Monday, December 26, 2011
BBC News - DIY $1 solar panel maker heads to Africa for charity
'via Blog this'
Friday, December 16, 2011
Why programmers work at night
This is why programmers are so annoyed when you distract them."
A geek with a hat » Why programmers work at night:
'via Blog this'
Friday, December 9, 2011
Tuesday, December 6, 2011
Friday, December 2, 2011
Inside DreamHack, the 12,000-computer LAN party - Slideshow | ExtremeTech
'via Blog this'
Tuesday, November 22, 2011
Friday, November 4, 2011
BBC News - Changes to the world's time scale debated
And the main issue up for debate is the leap second - and whether we should abolish it.
The leap second came into existence in 1972. It is added to keep the time-scale based on atomic clocks in phase with the time-scale that is based on the Earth's rotation."
'via Blog this'
Thursday, November 3, 2011
Sunday, October 23, 2011
Computer game solves AIDS mystery - IDG.se
Computer game solves AIDS mystery - IDG.se:
'via Blog this'
Wednesday, October 19, 2011
Android 4.0 Platform | Android Developers
for details: Android 4.0 Platform | Android Developers:
'via Blog this'
Saturday, October 8, 2011
IT Industry Competitiveness Index 2011
Saturday, October 1, 2011
70 Things Every Computer Geek Should Know. | Arrow Webzine
1. Default Password List
One of the best list of default passwords. http://www.searchlores.org/defpasslist1.htm 1A. Usability of passwords http://www.baekdal.com/tips/password-security-usability.2. A bit, about How to hack some common gadgets.
If you rolled your eyes here, that is a good thing. If not, you have many things to learn, young padawan. It’s amazing how few people know how to do this. If you’re unsure, hit up the link below to find out how: http://www.aagneyam.com/blog/?cat=708
3. Identify Keyloggers
Internet cafes are the most likely place you’ll find them, followed by library, perhaps, and maybe even you own house if you’ve some unscrupulous friends/family. Identity theft groups warn about keyloggers and advocate checking out the keyboard yourself before continuing. Can you identify a keylogger, however, if one is plugged into the back of the system? Here’s what one looks like: Hit up this link for excellent info on keyloggers on public computers and how to protect yourself: , http://www.ghacks.net/2007/06/28/how-to-defeat-most-keyloggers-on-public-computers/
4. Surf the Web Anonymously
We won’t make any assumptions about why you may need this particular skill, but the fact remains that every geek should know how to traverse the Internet with the highest amount of security possible. Aside from the safest method–which is using a connection that is not yours–you will need the ultimate in proxies…Tor. Tor is an onion-routing system which makes it ‘impossible’ for someone to find out who you actually are.
5. Bypass a Computer Password on All Major Operating Systems
Obviously you shouldn’t use this to gain unlawful access to a computer. If you’re a geek, however, you’ll eventually end up in a situation where someone forgets their password, you acquire a machine with an operating system you cannot access, or similar situation. See this tutorial for info on how to bypass the password on the three major operating systems: Windows, Mac, and Linux. http://www.joetech.com/2009/01/29/how-to-crack-the-account-password-on-any-operating-system/
6. Find a Users IP Address on AIM
Knowing someones IP address is actually pretty useless in this case, but most people don’t realize that. If someone is harassing you via AIM and you can’t get them to stop, discovering their IP and sending it to them–with a nicely worded threat of law enforcement involvement should they not stop–is likely enough to send them scamping away with tail between legs. http://www.ehow.com/how_5529416_someones-ip-address-aim-chat.html
7. Hide a File Behind a JPEG
So you need a nice spot to hide your blackmail personal files. You could, of course, bury them deeply within a series of random, useless folders, but there’s always the chance of them being discovered. A password protected RAR is the best choice, but it’s a bit obvious despite the most boring title you could give it. A sneaky person would hide the important file behind a completely random and boring family reunion photo, where no person in their right mind would shift through. http://www.online-tech-tips.com/computer-tips/hide-file-in-picture/
8. Crack a Wifi Password
This is one of those things you don’t need to do (hopefully), but that you still need to know just for the sake of knowledge. A strong WPA password is very secure, but most people don’t want to bother learning a convoluted series of letters, numbers, and symbols, instead opting for random everyday words. A good overall tutorial on wifi and cracking can be found here: http://www.aagneyam.com/blog/?p=623
9. Monitor Network Traffic
The Internet is a vast place with a bit of everything. Whether you’re curious about what your roommate is downloading, your kid is getting into, or any leeches living around you who’ve unscrupulously breached your wifi, knowing how to analyze network traffic is an invaluable skill. Here is a list of dozens of network analyzers, as well as some general info to get you started: http://www.slac.stanford.edu/xorg/nmtf/nmtf-tools.html
10. Recover Master Boot Record
'via Blog this'
Swedish app developers to pay VAT twice - The Local
The VAT burden could end up being as much as 25 percent, making it very hard for Swedish companies to be competitive, according to developers, especially as these rules do not apply to those in other EU countries."
'via Blog this'
Monday, September 26, 2011
Quantum Diaries
And there, surprise! The neutrinos reached the Gran Sasso laboratory 60 nanoseconds (i.e. 60 billionth of a second) faster than light travelling over the same distance, even though neutrinos are expected to travel slightly below the speed of light."
read more: Quantum Diaries:
'via Blog this'
Wednesday, August 31, 2011
Wednesday, August 24, 2011
Sunday, August 21, 2011
Thursday, August 11, 2011
A beginner's guide to caching data in Drupal 7 | Lullabot
One solution is to turn on page caching on Drupal's performance options administration page. That speeds things up for anonymous users by caching the output of each page, greatly reducing the number of DB queries needed when they hit the site. That doesn't help with logged in users, however: because page level caching is an all-or-nothing affair, it only works for the standardized, always-the-same view that anonymous users see when they arrive.
Eventually there comes a time when you have to dig in to your code, identify the database access hot spots, and add caching yourself. Fortunately, Drupal's built-in caching APIs and some simple guidelines can make that task easy."
details on : A beginner's guide to caching data in Drupal 7 | Lullabot:
Monday, August 8, 2011
Computable Document Format for Interactive Content
Launched by the Wolfram Group, the CDF standard is a computation-powered knowledge container—as everyday as a document, but as interactive as an app.
Adopting CDF gives ideas a broad communication pipeline—accelerating research, education, technical development, and progress."
From:Computable Document Format for Interactive Content
Sunday, August 7, 2011
Friday, August 5, 2011
Reverse Ajax, Part 2: WebSockets
A WebSocket URL is started by typing ws:// or wss:// (on SSL).
The timeline in Figure 1 shows communication using WebSockets. An HTTP handshake is sent to the server with specific headers. Then, a type of socket is made available either on the server or on the client side in JavaScript. This socket can be used to asynchronously receive data through an event handler."
for Detaila: see Reverse Ajax, Part 2: WebSockets:
Create GPS-enabling web applications
for details: Create GPS-enabling web applications:
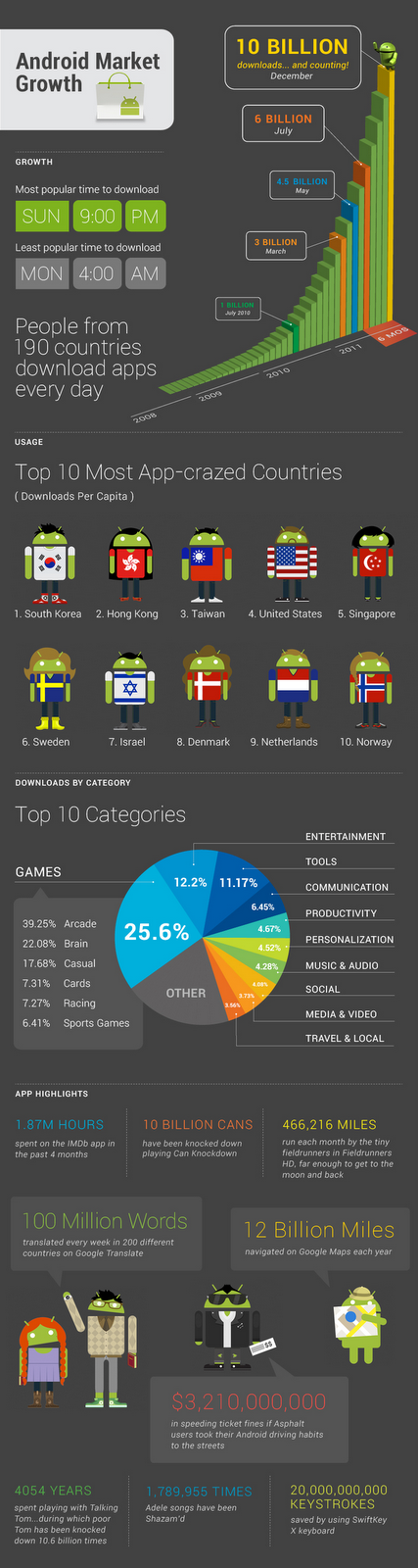 10B_2_lg.png (427×1600)/>:
10B_2_lg.png (427×1600)/>: